Relay Binary
LetUsMsg relays are single static binaries — no external dependencies, minimal RAM, and designed to be ephemeral so you can recreate or rotate them quickly. Supported builds: Linux AMD64, Linux ARM64, macOS Intel, and macOS Apple Silicon.
- Simple static binary (
lum-relay) - Non‑root, zero data retention, zero disk writes
- No database, No cloud services, No websockets, No API
- Client -> relay protocol is HTTP/2 with mutual auth TLS (gRPC)
Download Relay
Download the file for you architecture, rename to ’lum-relay’, chmod 775, and execute
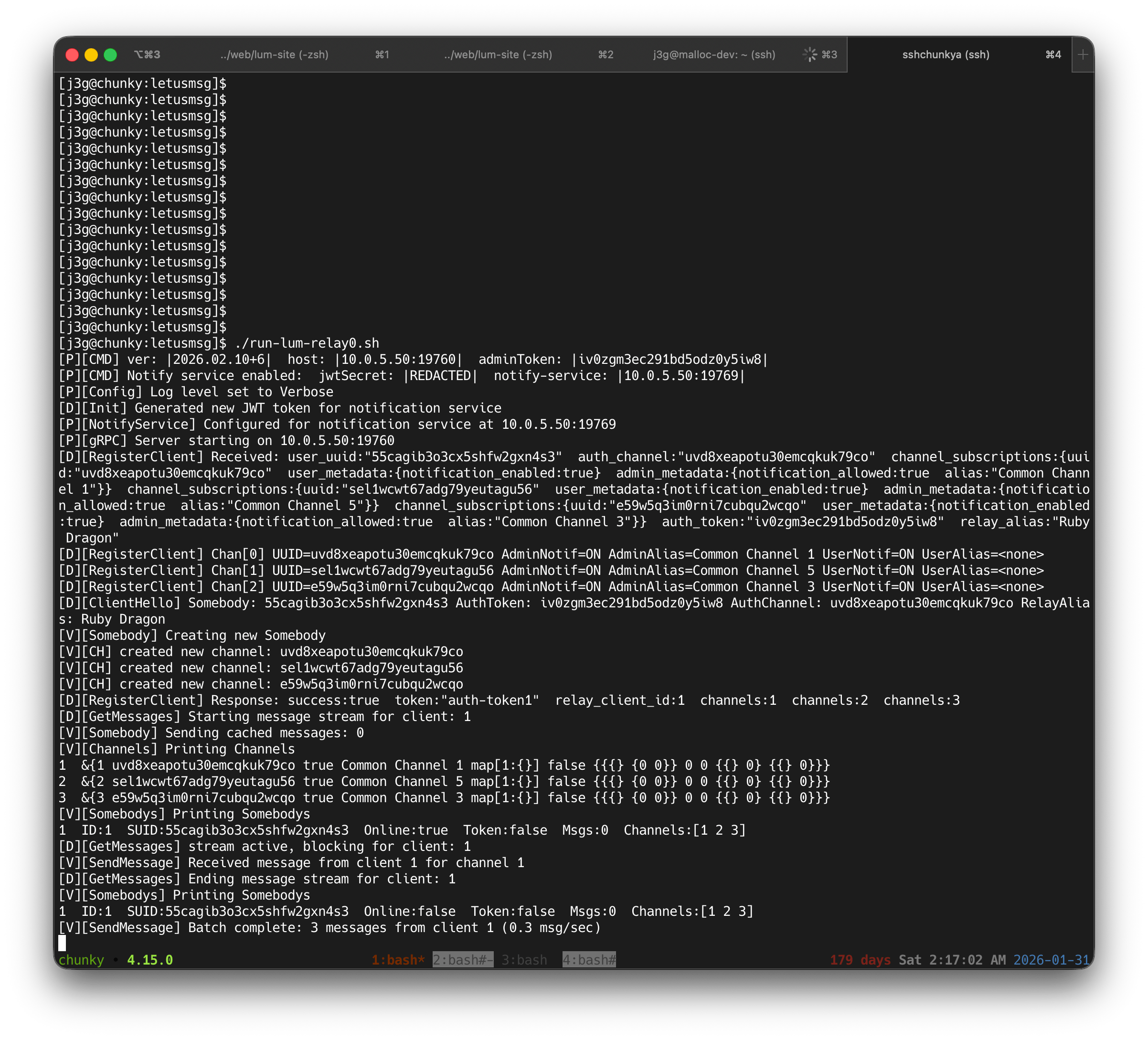
Run relay service
lum-relay
Run in a self-documenting script with env variable (better security)
run-lum-relay.sh
#!/bin/bash
# local service IP:Port
export HOST=10.0.5.50
export PORT=19760
# Token to authenticate you are admin
# use this token to add a relay
export ADMIN_TOKEN=iv0zgm3ec291bd5odz0y5iw8
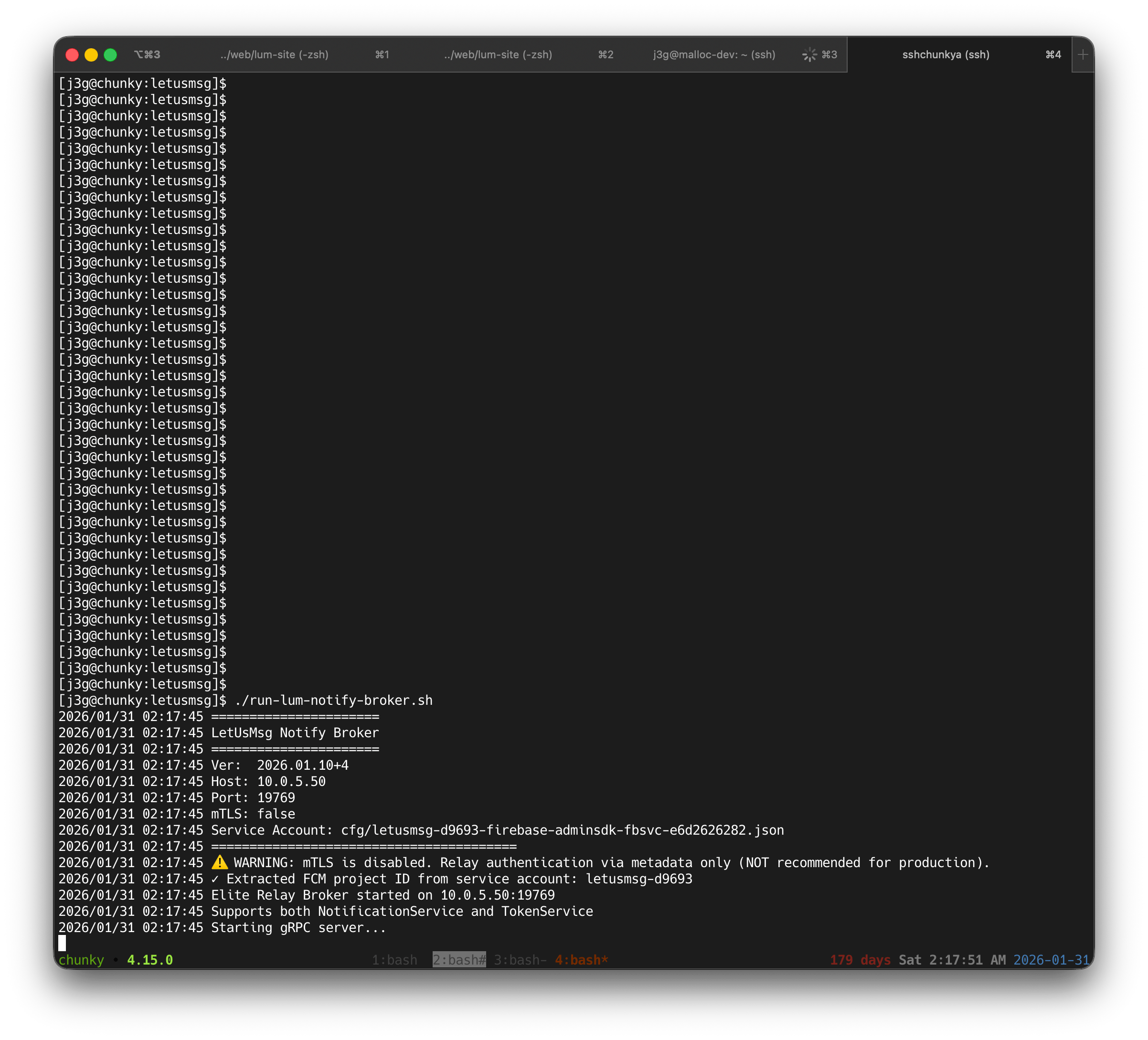
# IP:Port for the notification relay service
# The below IP:Port is a service provided by LetUsMsg Corp
# Note: notification relay service is optional, depending on your security requirements
export NOTIFY_HOST=dev.malloc.io
export NOTIFY_PORT=19769
# Auth token for notify relay service
# this value is for beta / demo purposes
export JWT_SECRET=test-secret-key-at-least-32-chars-long-for-security
./lum-relay start -v "$@"
lum-relay start
Command line example:
./lum-relay start -s 10.0.5.50 -p 19760 -t iv0zgm3ec291bd5odz0y5iw8 -v
Previous Releases
Linux AMD64
- lum-relay-amd64-linux-20260210
- lum-relay-amd64-linux-20260205
- lum-relay-amd64-linux-20260110
- lum-relay-amd64-linux-20260105
- lum-relay-amd64-linux-20260101
Linux ARM64
- lum-relay-arm64-linux-20260210
- lum-relay-arm64-linux-20260205
- lum-relay-arm64-linux-20260110
- lum-relay-arm64-linux-20260105
- lum-relay-arm64-linux-20260101
macOS Intel
- lum-relay-amd64-mac-20260210
- lum-relay-amd64-mac-20260205
- lum-relay-amd64-mac-20260110
- lum-relay-amd64-mac-20260105
- lum-relay-amd64-mac-20260101
macOS Apple Silicon
- lum-relay-arm64-mac-20260210
- lum-relay-arm64-mac-20260205
- lum-relay-arm64-mac-20260110
- lum-relay-arm64-mac-20260105
- lum-relay-arm64-mac-20260101
Default Rotation and Lifetimes
| Parameter | Default | Description |
|---|---|---|
| Relay TTL | 7 days | Automatic rotation |
| Grace period | 48 h | Overlap window for message pulls |
| Message TTL | 72 h | Cache expiry |
| Cipher rounds | 100 (default) | Configurable per channel |
Own your infrastructure. Control your encryption. Leave nothing behind.